Recent disclosures concerning Charming Kitten go beyond identifying operational infrastructure and campaign activity, pointing instead to internal documents that directly reflect the design and operational use of espionage tools. Among these materials, a preliminary report on a remote access tool known as RAT-2Ac2 provides a rare view into how a state-aligned RAT is built, deployed, and used in practice. This perspective moves beyond malware analysis to address the organizational logic underlying its development.
The internal report describes RAT-2Ac2 not as an experimental or conceptual sample, but as a fully operational system designed for controlling victim devices, managing multiple targets simultaneously, and enabling continuous monitoring. Detailed descriptions of the client–server architecture, operator panels, deployment workflows, and the range of surveillance capabilities indicate that this tool was part of a professional intelligence-collection cycle rather than an ad hoc or individual effort.
Examining RAT-2Ac2 is significant in that it shows how Charming Kitten develops remote access tools as structured, scalable systems that directly serve the needs of surveillance operators. The remainder of this article analyzes the technical and operational aspects of this RAT to clarify how such tools become the backbone of covert digital surveillance and long-term control over selected targets.
RAT-2Ac2; Preliminary Technical Report on a Modular Remote Access Tool
RAT-2Ac2 is documented in an internal “preliminary report” dated March 2023, which describes a fully operational remote access tool designed for victim device control and data collection. Rather than presenting a generic overview, the report details concrete implementation aspects, including system architecture, deployment requirements, operator-facing panels, and a catalog of supported commands and modules.
The report describes a client–server design in which the client component is implemented in .NET/C#, while the server backend is developed in Python using the Flask framework. Communication is routed over HTTPS and supported by a relay-based infrastructure, allowing operators to manage multiple infected clients through a centralized control panel.
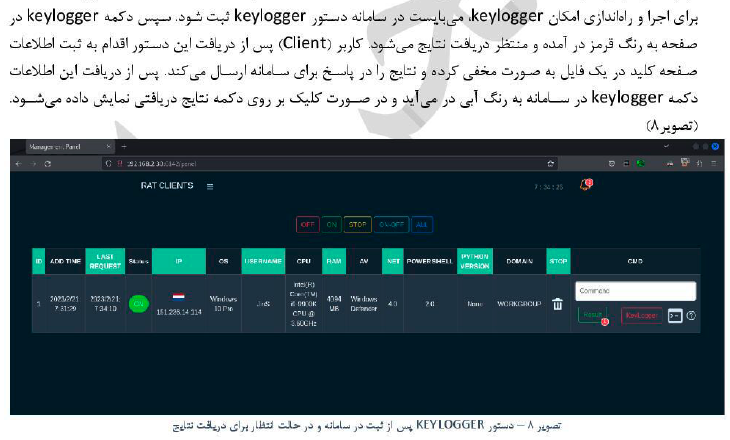
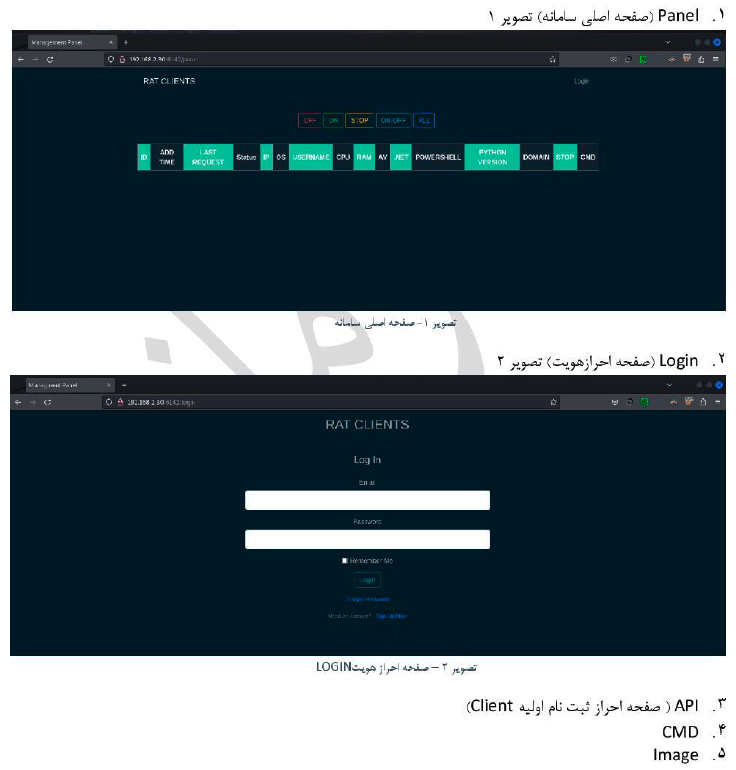
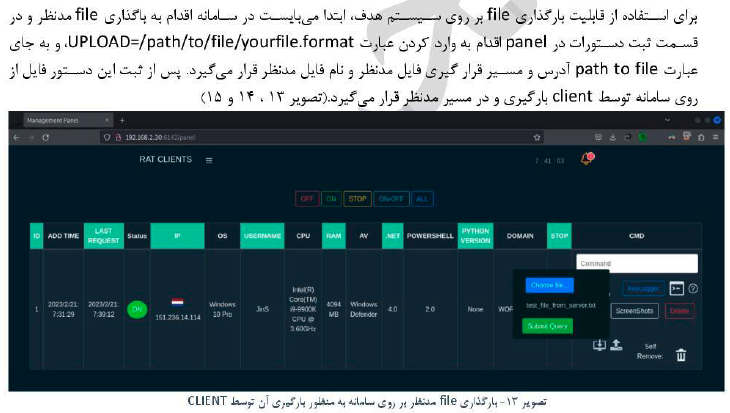
Functionally, RAT-2Ac2 provides core surveillance and control capabilities commonly associated with remote access trojans. These include remote command execution via a shell interface, file upload and download, remote desktop control through VNC, and keystroke logging. The report also documents system profiling features, including the collection of device and environment attributes such as operating system details, hardware characteristics, network identifiers, and installed security products.
Beyond its core capabilities, the report highlights operational mechanisms intended to support stealth and traffic management, including configurable manipulation of network request headers. The inclusion of server setup instructions and deployment workflows indicates that RAT-2Ac2 is not a conceptual prototype, but a tool intended for real-world operational use, providing a structured interface for persistent access, continuous monitoring, and staged tasking against targets.
