In autumn 2025, a series of coordinated disclosures published by the KittenBusters project provided the first systematic exposure of the operational infrastructure associated with the Charming Kitten advanced persistent threat (APT35). Rather than focusing on isolated incidents or attribution claims, these disclosures mapped the group’s active phishing domains, malware delivery pipelines, command-and-control infrastructure, and a portfolio of bespoke surveillance tools deployed across multiple campaigns. This shift toward infrastructure-level documentation marked a turning point in how Charming Kitten’s operations could be understood, analyzed, and contextualized.
Charming Kitten has long been assessed by independent researchers as a state-aligned threat actor operating in close coordination with Iranian security institutions. Multiple investigations have linked its campaigns, targeting priorities, and operational timing to the intelligence objectives of the IRGC Intelligence Organization, often referenced internally as Unit 40. Subsequent leaks and analyses have further demonstrated how Charming Kitten’s tooling intersects with broader Islamic Republic’s surveillance strategies.
Among the data leaked from Charming Kitten’s operational infrastructure, what stands out most is not a single piece of malware, but a design pattern centered on tools built for sustained surveillance, long-term access, and behavioral control. These disclosures show that Charming Kitten operates beyond the model of an isolated hacking actor, instead deploying a collection of modular tools, each functioning as part of a larger surveillance ecosystem. Within this ecosystem, deceptive access, persistence, and data extraction are deliberately designed as tightly interwoven components.
One prominent example of this ecosystem is a Windows-based Remote Access Trojan (RAT) built on a modular architecture and a relay-based command-and-control system (C2). The design of this tool enables flexible capability management, concealment of the true origin of communications, and the maintenance of access even under conditions of infrastructure disruption. Such characteristics make clear that this RAT was not developed for rapid intrusion or episodic attacks, but for the continuous monitoring of selected targets.
Examining this tool provides a critical window into Charming Kitten’s operational logic: the use of malware that avoids drawing attention by embedding itself within ordinary layers of the operating system, and by relying on legitimate Windows utilities to conceal malicious activity behind the appearance of normal behavior. The following analysis examines this modular Trojan from a technical and structural perspective, illustrating how such implants are engineered to serve long-term intelligence and surveillance objectives.
Modular Windows RAT with Relay-Based C2
One of the core tools uncovered through the Charming Kitten internal disclosures is a Windows-based RAT built around a modular architecture. The malware is composed of multiple interoperable components coordinated by a central controller module, commonly referred to as main. This primary module manages execution flow, communication with C2 infrastructure, and the activation of auxiliary modules responsible for data collection and system interaction.
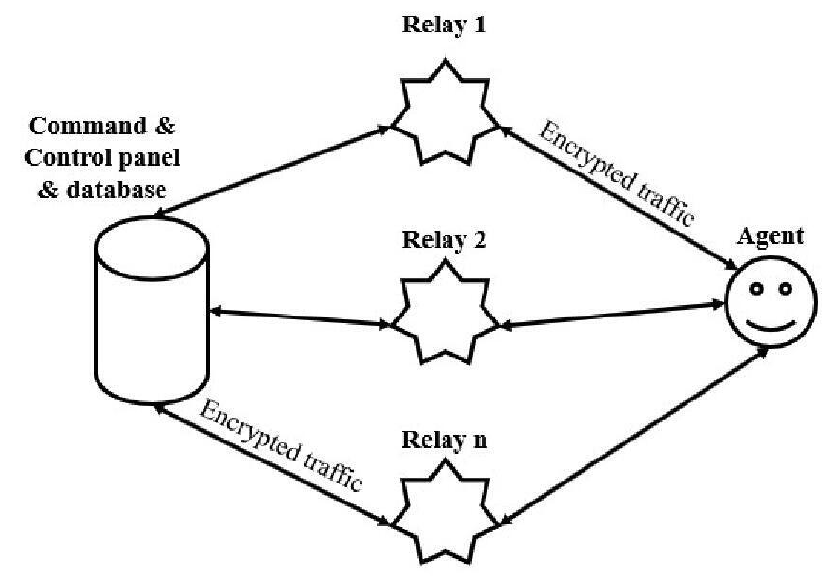
The RAT supports both direct and indirect communication with its operators. In indirect mode, traffic is routed through intermediary relay servers, a design choice that obscures the origin of commands and increases operational resilience against takedowns and attribution. This relay-based C2 architecture enables sustained access even when individual nodes are disrupted.
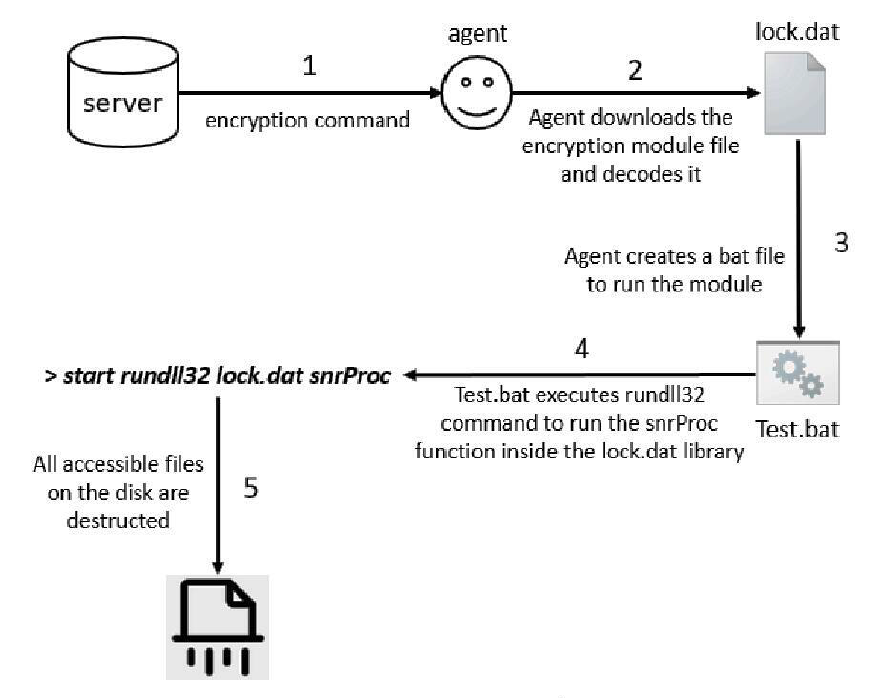
Functionally, the malware provides full remote control capabilities, including command execution, file upload and download, and dynamic tasking. Its modular design allows operators to selectively deploy functionality depending on the target profile. Identified modules include components for credential harvesting, keylogging, browser data extraction, and targeted data collection from specific applications such as messaging platforms. Evidence of persistence mechanisms indicates that the malware is designed to survive system reboots and maintain long-term access to compromised devices.
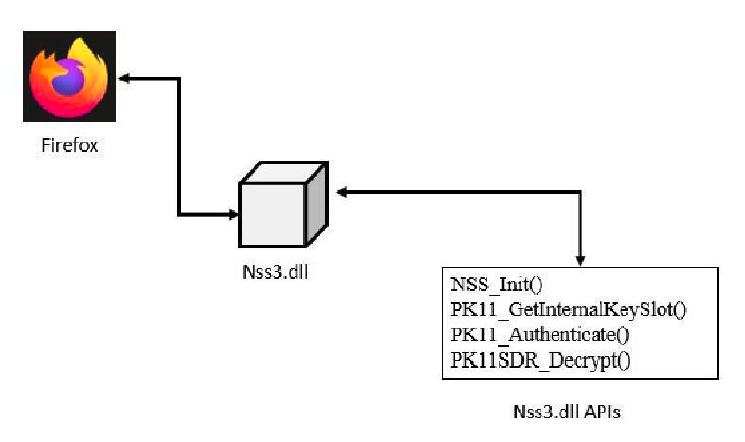
Technical analysis shows that execution is frequently achieved through legitimate system utilities such as rundll32.exe, a technique commonly used to evade basic security controls by blending malicious activity with normal operating system behavior. Data collected from victims is stored locally in structured files and exfiltrated through the established C2 channels.
Taken together, this tool represents a mature, state-aligned surveillance implant rather than an opportunistic cybercrime utility. Its architecture, feature set, and operational discipline are consistent with long-term espionage objectives, reinforcing assessments that Charming Kitten functions as an advanced persistent threat engaged in sustained monitoring of targeted users.
